At a Glance Censys vs Shodan
To get actionable and trustworthy insights, you need internet data that’s complete, accurate, and up-to-date. Censys outperforms Shodan across all three:
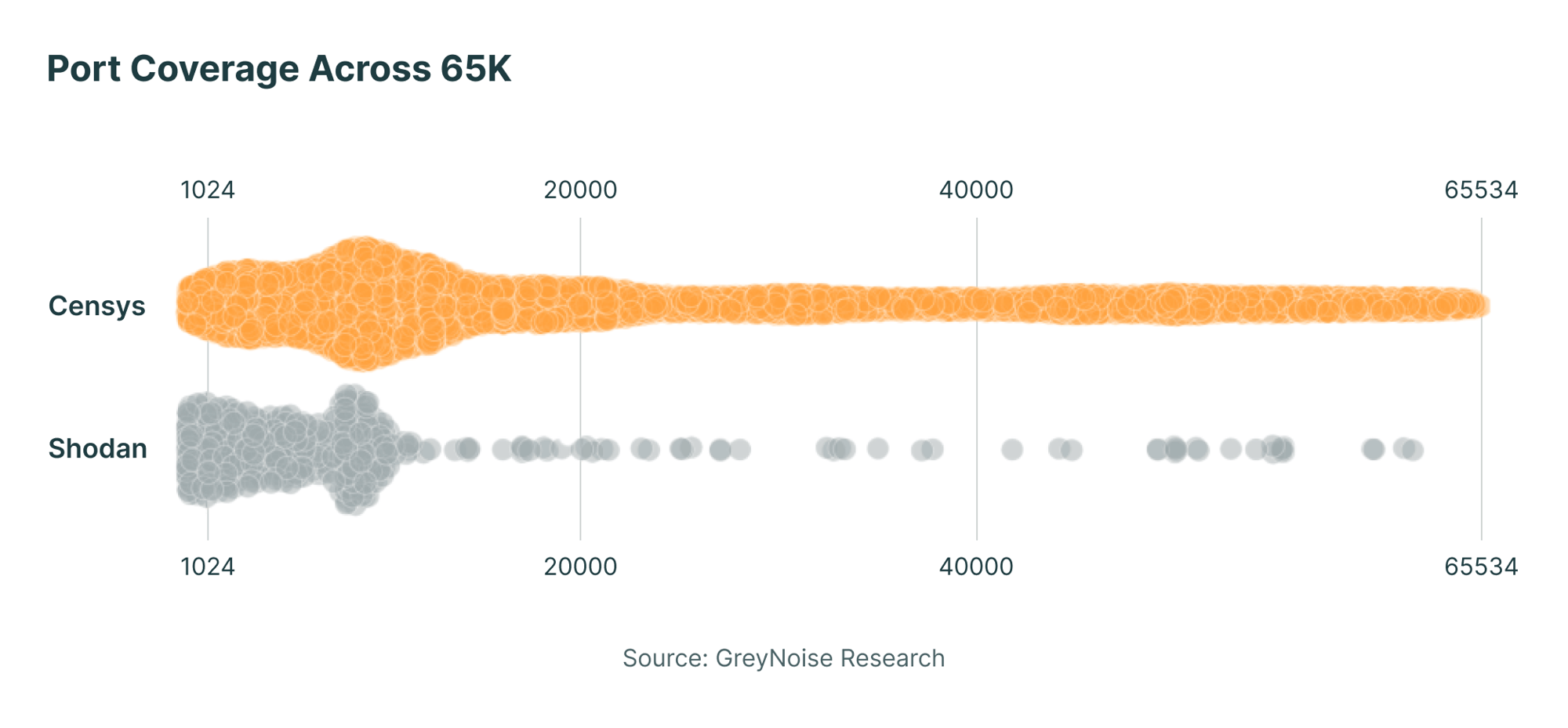
- 8x more visibility across all 65K ports
- 4x fewer stale or duplicate results
- 7x faster discovery of infrastructure changes
Reach out to our sales team to see firsthand how Censys out performs Shodan →
See the Difference
The Consequences of Inferior Data
With incomplete, slow, and stale internet intelligence, you create an invisible, unmanaged attack surface that only attackers can see.
Millions of customer records stolen. Double-digit stock drops in a single day. Years of brand damage.
Global regulatory investigations. Class-action settlements in the millions of dollars. Exposed intellectual property. Dead deals with risk-averse buyers.
Forced leadership changes. Loss of major customers. Permanent hit to your organization’s security credibility.
Censys is THE Authority for Internet Intelligence
Censys sets the Industry benchmark for Internet scanning by combining breadth of discovery with fast, accurate, and continuously refreshed data.
Download the Censys vs. Shodan comparison sheet below to see why stronger security starts with Censys.
Censys captures 8x more services than Shodan across the complete 65K port space. Non-Standard and high number ports commonly are exploited by attackers and the source of Shadow IT so you need to see it all.
With Censys, 92% of listed services are live, compared to just 68% in Shodan. The internet evolves quickly. Stale or duplicate data creates noise, false positives, and worse, a false sense of security.
Censys detects new services in <24 hours whereas Shodan requires ~3 days. Services appear and disappear quickly so fast discovery is critical to minimize risk.
Trusted by Security Teams Worldwide Industry, Governments, & Security Companies Rely on Censys




We had a 35% improvement in time to detection and efficacy for a certain APT group through automated infrastructure ingestion with Censys.

